Why HTTPS Doesn't Protect From Phishing Attacks and MitM Exploits
by David Rihak, Peig.io
HTTPS is like the internet’s safety net—it encrypts data so no one can snoop on your online activity. You probably think HTTPS is the reason you can shop, bank, or send messages without worrying about someone spying on you. But here’s the catch: HTTPS isn’t perfect. Unfortunately, cybercriminals have clever ways to exploit it, especially with a type of attack called Man-in-the-Middle (MitM). Let’s break down how this works and why it’s such a big deal.
Why MitM Attacks are Significant
MitM attacks occur when an attacker intercepts and possibly alters the communication between two parties without their knowledge.
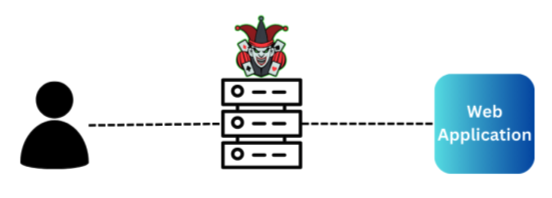
Here’s why they are particularly concerning in the context of HTTPS, especially when users authenticate to bad-actor websites:
1. Exploitation of User Trust
Attackers leverage social engineering and fake websites to mimic legitimate HTTPS secured platforms. Users often fail to notice subtle differences in domain names (e.g., using "rn" instead of "m") or miss HTTPS indicators, leading them to authenticate on malicious sites. Once users enter their credentials, attackers capture this sensitive information and can impersonate the user on the actual site.
2. Phishing and Fake HTTPS Sites
Phishing campaigns often use HTTPS to appear trustworthy. Modern browsers emphasize the presence of HTTPS with padlock icons, but these indicators alone do not guarantee that the site is legitimate. Bad actors purchase domain certificates for fake websites, enabling them to deceive users into thinking they are on the correct platform.
3. DNS Spoofing to Redirect Traffic
Attackers can manipulate DNS responses to redirect users to malicious sites that closely mimic legitimate ones. Even though HTTPS secures the connection, it doesn’t prevent users from authenticating on fraudulent domains.
4. TLS Stripping in Conjunction with Phishing
An attacker might use a TLS stripping attack to downgrade an HTTPS connection to HTTP, allowing them to intercept and manipulate traffic. Users may not notice the lack of HTTPS if they are focused on the content or appearance of the website, especially if the site design mimics the real one.
5. Credential Harvesting and Session Hijacking
Once users authenticate on a bad-actor website, attackers can harvest login credentials and session cookies. These are often reused to access legitimate accounts, bypassing additional security mechanisms.
How These Attacks Are Achieved
1. Crafting Realistic Fake Websites
Attackers purchase domains that are visually similar to trusted domains, often exploiting typos (e.g., "g00gle.com" instead of "google.com"). They obtain legitimate SSL/TLS certificates for these domains to make them appear secure.
2. Leveraging Phishing Emails
Phishing emails are tailored to look like legitimate communications from trusted organizations. They often include links to fake HTTPS-enabled websites, prompting users to authenticate.
3. Setting Up Rogue Wi-Fi Networks
Attackers create open Wi-Fi networks in public places. Once a user connects, all traffic can be redirected to malicious servers or fake websites. Even if HTTPS is present, users may inadvertently authenticate on fake domains.
4. Exploiting Certificate Authorities
In rare cases, attackers compromise CAs to issue legitimate-looking certificates for fake domains. These certificates deceive even the most vigilant users and browsers, enabling seamless MitM attacks.
5. Using Malware and Browser Extensions
Malware or malicious browser extensions can manipulate a user’s browser or DNS settings, redirecting them to bad-actor websites even when they type the correct URL.
Mitigating MitM Attacks with the Device-bound Access Security Model
One promising approach to mitigating MitM attacks is adopting a device-bound access security model. This model ties user authentication to a specific device, ensuring that user credentials are bound to a single authorized device, allowing access only for devices that can provide a reliable proof of possession of their device-bound credentials. Thus effectively making the device the credential.
Device-bound models significantly reduce the risk of MitM attacks by making it impractical for attackers to exploit stolen credentials.
Conclusion
Man-in-the-Middle attacks targeting user authentication on malicious websites are a significant threat to internet security. By exploiting trust in HTTPS, attackers can steal sensitive credentials and impersonate users. Understanding these attack vectors and implementing strong mitigation measures is essential for minimizing risks and ensuring safer online experiences.